It does whatever
you want
No system is like any other. The TKey-concept opens up for adapting TKey for any use case

Radically
Open Source.
Open Mind, Open Code.

Made in Sweden
Works everywhere

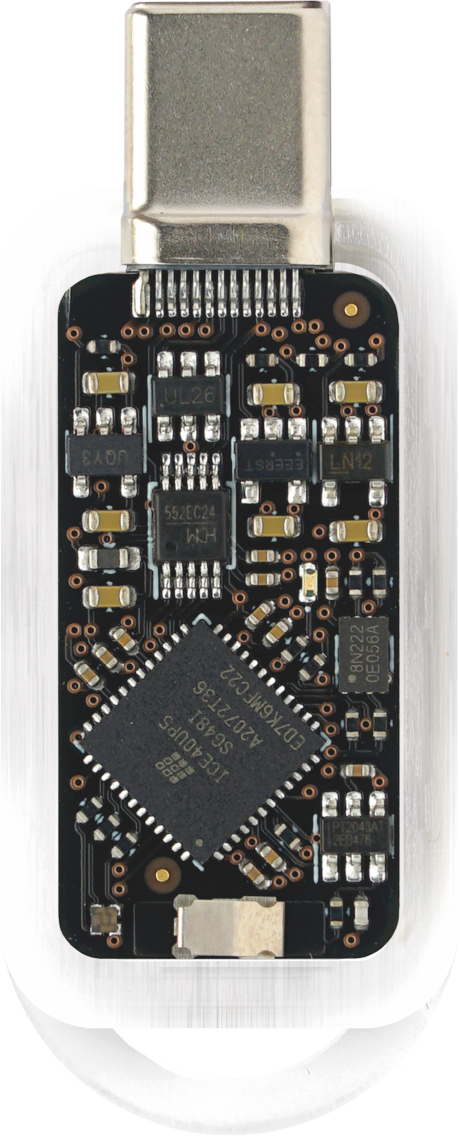
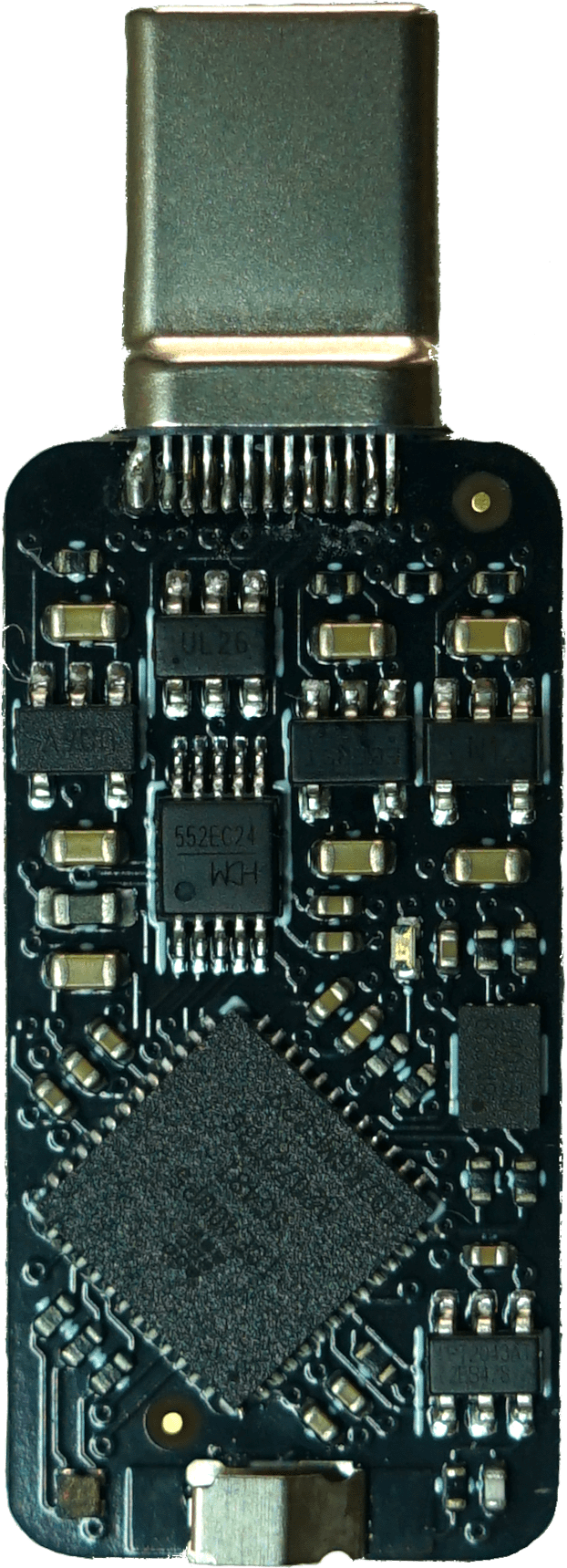
TKey is a compact USB-C device designed to provide a secure and isolated environment for specialized applications. Applications are loaded onto TKey and run one at a time in complete isolation, preventing access to the secrets of other applications. This design ensures digital protection for critical tasks such as Authentication, Digital Signing, Secure Random Number Generation, and Encryption.
A new kind of security key.
Radically Open Source.

Measured Boot
With measured boot the integrity of the application running on TKey is guaranteed. By the way, we think computers should be booted this way.

Flexibility
No system is like the other. The TKey-concept opens up for adapting TKey for any use case. With our code being open source, there is a lot of inspiration to find and give you a jumpstart for your adaptions.

Community
We think of people and organisations who buy TKey as part of a community that, like us, are engaged for improving cyber security.
Shop
We currently ship to countries within EU/ESS, USA, Canada, Australia, New Zealand.
From our blog
Copyright © 2022 - 2025, Tillitis AB
Template by Bootstrapious. Ported to Hugo by DevCows.